TL;DR: Scroll to the bottom for a howto.
Background
Ubuntu usability bug
Ubuntu has a long-standing usability bug, where a user can elect to use full disk encryption for their Ubuntu installation, and will be offered to save a recovery key, but the recovery key will not exist once the user is finished with their installation.
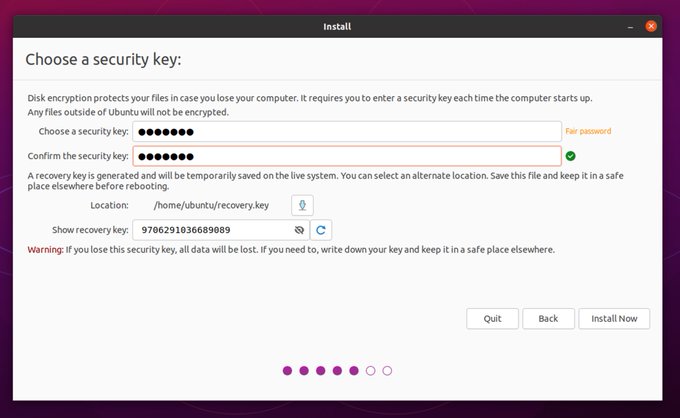
The default recovery key location will not exist once the user reboots to their new system
When choosing how to save the recovery key, the initial proposition to the user is to store the key in a non-persistent location. No obvious persistent storage is offered to the user at any point during the installation, nor is the user warned that they are saving the recovery key to non-persistent storage. This issue is worth of it’s own blog post about how to design for humans… but let’s leave it alone.
The reason I mention this bug, is because my local support team requested that I give them a recovery key for my work laptop, which is normal procedure around here. I’m happy to oblige, but first I had to create an actual recovery key…
Finding the happy path
My Ubuntu 22.04 is installed with root-on-ZFS and full disk encryption. OpenZFS has native support for full disk encryption, however GRUB will not work with ZFS directly – therefore, Ubuntu uses an intermediary LUKS encrypted EXT4 partition to store the ZFS encryption key. I had to find this out from the #ubuntu channel on irc.libera.chat from a user who also figured it out on their own.
Finally, lets get to the meat of the matter…
How to manage encryption passphrases on an Ubuntu 22.04 with root-on-ZFS and full disk encryption
- The ZFS encryption key is stored in the
POOLNAME/keystoreZFS volume. The default for root-on-ZFS isrpool/keystore. - The
rpool/keystorezfs volume is mounted at/run/keystore/rpool. Backup this file to be able to unlock the ZFS volume itself. - The
rpool/keystoreoriginates from /dev/zd0, which is the LUKS volume GRUB actually unlocks to proceed with the whole magic of using native ZFS encryption.
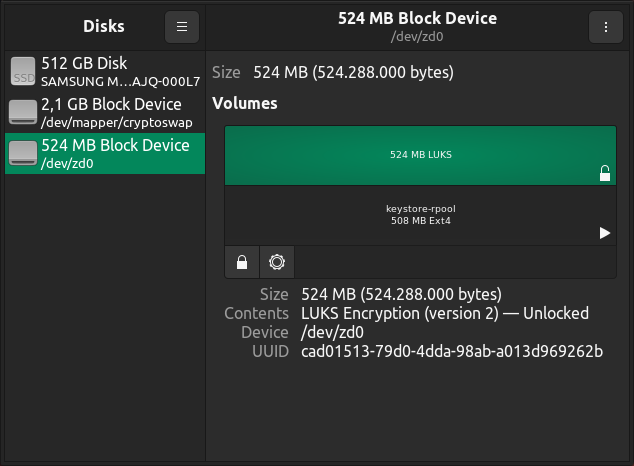
The encryption key is stored on a LUKS volume
Howto
To manage your encryption keys:
sudo cryptsetup luksDump /dev/zd0to view your existing keyslotssudo cryptsetup luksAddKey /dev/zd0to add a keysudo cryptsetup open --test-passphrase /dev/zd0to test your newly added LUKS key
That is about it.
Afterword
I really wish Ubuntu would have had some native tool, or at least documentation, on this matter. root-on-ZFS was introduced as an “EXPERIMENTAL” in Ubuntu 19.10 and Ubuntu 20.04, however it has been long enough that at least some documentation on the matter should have precipetated by now. For that, there is this blogpost.